It’s about IAM, not passwords
When it comes to cyber security, Zero Trust is hard to miss. The concept is at the heart of many organizations today and is far more than just a buzzword.
Almost every aspect of a business has to do with it. However, there is one component that is particularly important to Zero Trust. The title of this article suggests as much: It’s about digital identity and Identity Management. Knowing who exactly is using what device to access the corporate network is essential to protecting systems and data.
It’s time to go beyond passwords
How do you secure access and control of people who gain access? Surely, with username and password. But also, credentials can act as identification as well as a safeguard, so to speak.
But the truth is, passwords do not provide good protection. They can be stolen and compromised relatively easily. Excellent passwords that are extremely difficult to guess can be much harder to crack, but they can still be stolen.
Attack methods have become increasingly more developed. Once attackers have penetrated, they move freely through the network, capturing credentials, building backdoors, and gaining continued constant access to valuable data while spreading malware.
Multi-factor authentication
With the escalation of cyber-attacks in recent years, more attention is being paid to network security. Cyber security has moved up from IT to GL as an area of responsibility. However, moving beyond basic authentication is not yet a reality for many enterprises, and Single Sign-On (SSO) is far from universal.
Proof of this is the seemingly endless list of password-based security breaches we find on the Internet every day. While many organizations are trying to mitigate the risks associated with passwords by adopting two-factor authentication (2FA) or multi-factor authentication (MFA). This promises a significant improvement in security, and that is correct, but there are differences.
Securing with a text message via SMS or email with a six-digit verification code, for example, poses a risk if a malicious user already has access to an employee’s email or phone number.
More advanced MFA frameworks cannot guarantee 100% security because device biometrics cannot truly prove a user’s identity. And if MFA doesn’t work or a person can’t perform multi-factor authentication for some reason, there are fallback options like a one-time text code (one-time password) that provides another avenue of attack.
So how can an organization address the current security issues and achieve rock-solid security using the zero-trust framework?
Better protected by focusing on digital identities
What is clear is that the Zero Trust framework is based on the idea that you are constantly checking and consistently verifying. In the identity space, Zero Trust includes things like verifying a person’s physical location, device ID or valid certificates when logging in. This can detect when logins are made from a different IP address or at an unusual time. Things like this signal that something may be wrong, and the company can deny access until the security team can take a closer look.
Something like this is basically multi-factor authentication too, but it’s taken a step further. Context-aware and adaptive, and most importantly, user-friendly! The checks run in the background without the user noticing and without having to navigate through additional factors.
Achieving Zero Trust requires numerous tools, technologies, and processes, and after all, you have to start somewhere. Most importantly, it requires a shift in thinking about security. When companies get the identity component right, they suddenly take a big step closer to achieving their goal.
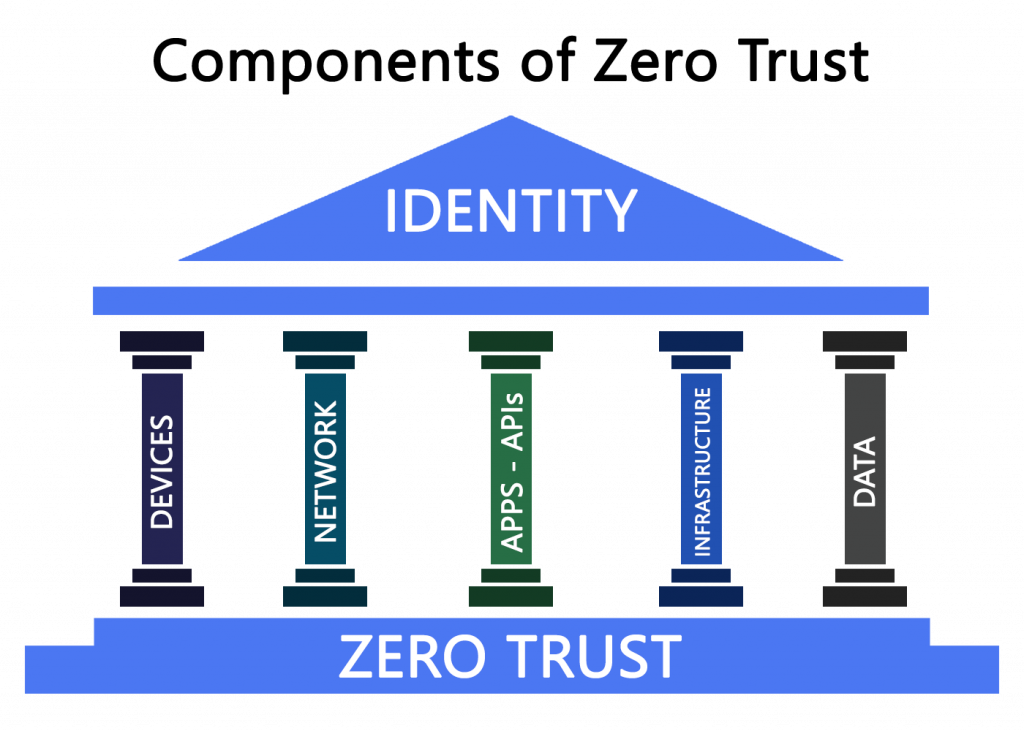
Here’s how IAM fits into the Zero Trust concept
In a network, knowing exactly who is doing what and why is essential to maintaining security. To do that, it’s just not enough to have a good firewall and trust every actor once he or she is in. This is why IAM is fundamental to successfully implementing a Zero Trust architecture.
It means that even authorized users must verify themselves (over and over again) when they move from one segment of the network to another, for example, or when they want to perform actions or view data that is subject to a higher level of security.
But isn’t that far too cumbersome? That’s exactly the crux of the question. In terms of security, the answer is clear: whether it’s inconvenient for users is irrelevant. But the reality is different. If it is too cumbersome, the users find detours or the whole system fails. Experience from hundreds of projects clearly shows that usability is not nice-to-have. It is not an enthusiasm factor, but a basic requirement. And this is not possible without IAM.
The community has widely accepted the Zero Trust philosophy, although, there is no comprehensive understanding of how to move from concept to reality. Nor are there universal standards for implementation. What is undisputed, however, is how important IAM is to Zero Trust implementation, as it is often the first step in an effective Zero Trust roadmap that is also accepted by users.
Where are enterprises at with implementation?
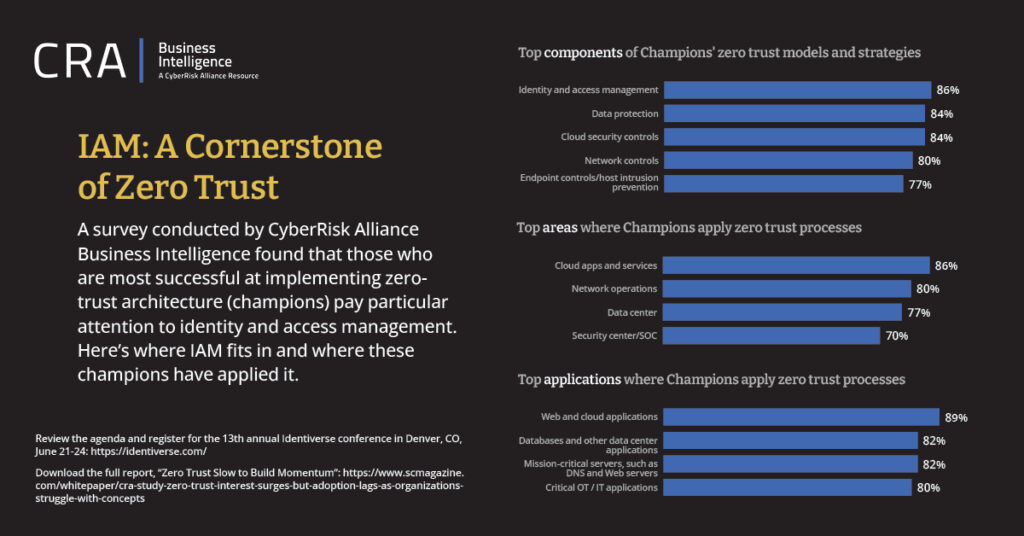
To measure how well organizations are doing in Zero Trust implementation, CRA Business Intelligence surveyed 300 IT and security decision-makers in January and February of 2022. The results of this survey showed, that once an organization has adopted the Zero Trust model, which focuses on giving individuals as few privileges as possible to do their jobs (least privilege principle), the risk of data breaches decreases.
Yet many organizations are slow to move to a Zero Trust model, despite the fact that more and more employees are working remotely and the outdated perimeter security model is becoming less important.
Zero Trust, after all, assumes that a threat can just as easily come from inside as from outside the network. This means that the outer perimeter no longer matters. A user must authenticate not only at the network perimeter, but also when moving from one part of the network to another, or when accessing documents or files with a higher security level.
In short, no user/device gets trusted completely. Each device and user must state and prove its identity, and that identity determines the level of access granted as well as their authentication.
According to Verizon Data Breach Incident Reports, most security breaches are due to stolen or compromised user credentials. Once a malicious actor has penetrated a network, they move through the network and attempt to gain new levels of access by bypassing detection mechanisms and impersonating a legitimate user. This is exactly the kind of movement that strong IAM policies and a Zero Trust architecture are designed to prevent.
IAM is at the center
Among survey participants, the CyberRisk Alliance identified 70 “champion” organizations that have successfully implemented the Zero Trust model. These tended to be mid to large-sized organizations that were primarily focused on reducing risks posed by remote employees. Among these champions, Identity and Access Management was the most commonly implemented component of the Zero Trust architecture. “Any attempt to access the network must be verified,” said one champion in an interview. “Never trust anything.”
💡 Quellen:
SCMedia “How identity and access management fits into zero trust”
